
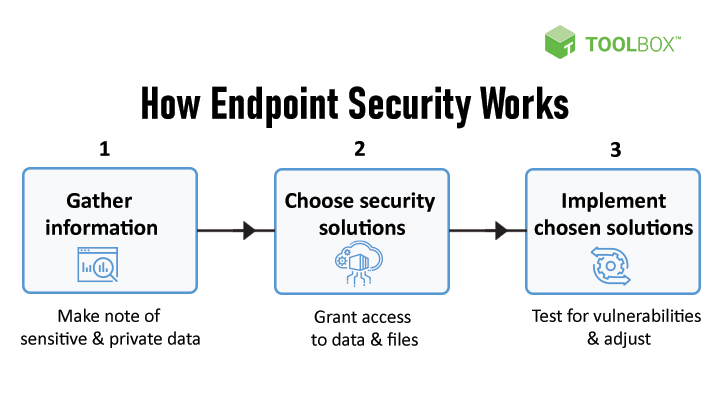
What Is Endpoint Security?
Endpoint security is the process of protecting devices like workstations, servers, and other devices (that can accept a security client) from malicious threats and cyberattacks. Endpoint security software enables businesses to protect devices that employees use for work purposes or servers that are either on a network or in the cloud from cyber threats.
The modern business landscape is seeing an increasing volume of cybersecurity threats from increasingly sophisticated cyber criminals. Hackers launch a cyberattack every 39 seconds, with a daily total of 2,244 attacks. Endpoints are one of the most common targets, given the sheer number of them in use to connect to networks. According to Strategy Analytics insight, there were already 22 billion connected devices in 2018, which is predicted to rise to 38.6 billion devices by 2025 and 50 billion devices by 2030. As a result, Verizon’s threat report found that up to 30% of data breaches involved malware being installed on endpoints.
Every endpoint that connects to the corporate network is a vulnerability, providing a potential entry point for cyber criminals. Therefore, every device an employee uses to connect to any business system or resource carries the risk of becoming the chosen route for hacking into an organization. These devices can be exploited by malware that could leak or steal sensitive data from the business.
In the face of this, it is imperative for businesses to deploy solutions that can analyze, detect, then block and contain cyber attacks as they happen. Organizations also need to collaborate with one another and utilize technologies that provide their IT and security teams with visibility into advanced threats, enabling them to quickly detect security risks for swift remediation of potential issues.https://www.youtube.com/embed/umB71Azc4XM?si=lHE9IFBrpgU_kcCu
Endpoint Security: A Comprehensive Guide to Protecting the Digital Frontier
Introduction
In an era where digital transformation is accelerating, the security of endpoints has become a focal point for organizations. Endpoints, including laptops, desktops, servers, and mobile devices, are the gateways to corporate networks and sensitive data. As the number of devices connected to the internet continues to grow, so too does the risk of cyber threats targeting these endpoints. This article provides a detailed examination of endpoint security, its importance, challenges, best practices, technologies, and future trends.
Chapter 1: Understanding Endpoint Security
1.1 What is Endpoint Security?
Endpoint security refers to a cybersecurity approach focused on protecting endpoints, such as user devices and servers, from cyber threats. Unlike traditional security measures that typically revolve around network perimeter defenses (e.g., firewalls), endpoint security emphasizes securing individual devices that connect to the network.
1.2 Importance of Endpoint Security
The rise of remote work, Bring Your Own Device (BYOD) policies, and an increasingly mobile workforce have transformed the security landscape. Endpoint devices often serve as entry points for cyberattacks, making them prime targets for hackers. Effective endpoint security solutions are essential for several reasons:
- Protection Against Cyber Threats: Endpoint security safeguards against malware, ransomware, phishing attacks, and other malicious activities targeting individual devices.
- Data Protection: Organizations store sensitive information on endpoints. Ensuring that this data is secure is crucial for compliance with regulations like GDPR, HIPAA, and PCI-DSS.
- Regulatory Compliance: Many industries have stringent regulations governing data protection. Effective endpoint security can help organizations meet these compliance requirements.
- Mitigation of Insider Threats: Endpoint security solutions can help detect and respond to suspicious activities from employees or contractors, reducing the risk of insider threats.
Chapter 2: Types of Endpoint Security Threats
2.1 Malware
Malware, short for malicious software, is any software intentionally designed to cause damage to a computer, server, or network. It includes viruses, worms, trojans, and ransomware. Endpoint devices are often infected with malware through email attachments, malicious downloads, or compromised websites.
2.2 Ransomware
Ransomware is a specific type of malware that encrypts files on an infected device and demands a ransom for decryption. Ransomware attacks have increased significantly, targeting organizations of all sizes and industries. The consequences of a successful ransomware attack can be devastating, leading to data loss, operational downtime, and financial losses.
2.3 Phishing Attacks
Phishing attacks involve deceptive emails or messages that trick users into revealing sensitive information, such as usernames, passwords, or credit card numbers. Phishing is a common method for cybercriminals to gain unauthorized access to endpoints.
2.4 Insider Threats
Insider threats occur when individuals within the organization, such as employees or contractors, misuse their access privileges. Insider threats can be intentional (malicious actions) or unintentional (negligent behavior), leading to data breaches or security incidents.
2.5 Unpatched Software Vulnerabilities
Outdated software can contain vulnerabilities that cybercriminals exploit to gain access to endpoints. Regular patch management is essential to protect devices from known security flaws.
2.6 Advanced Persistent Threats (APTs)
APTs are sophisticated, targeted attacks carried out by skilled adversaries. APTs often involve multiple phases, including reconnaissance, exploitation, and lateral movement within the network. Endpoints are often the first point of entry for APTs.
Chapter 3: Endpoint Security Technologies
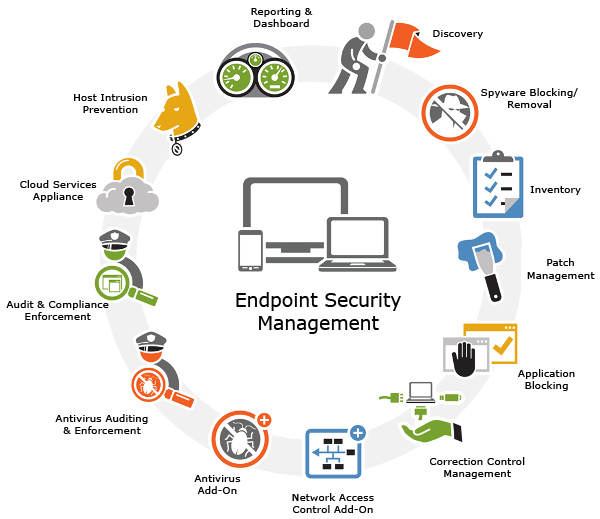
3.1 Antivirus and Antimalware Solutions
Antivirus and antimalware solutions are the foundation of endpoint security. These tools scan devices for known threats and provide real-time protection against malware. Modern solutions use heuristic analysis and behavior-based detection to identify previously unknown threats.
3.2 Endpoint Detection and Response (EDR)
EDR solutions provide continuous monitoring and response capabilities for endpoints. EDR tools collect and analyze endpoint data, enabling security teams to detect, investigate, and respond to suspicious activities in real time. EDR solutions often include threat hunting capabilities and incident response features.
3.3 Next-Generation Antivirus (NGAV)
NGAV solutions go beyond traditional antivirus capabilities by incorporating advanced technologies such as machine learning, behavioral analysis, and cloud intelligence. These solutions can detect and block sophisticated threats, including fileless malware and zero-day attacks.
3.4 Mobile Device Management (MDM)
MDM solutions enable organizations to manage and secure mobile devices used within the enterprise. MDM allows IT administrators to enforce security policies, deploy applications, and remotely wipe devices in case of loss or theft.
3.5 Data Loss Prevention (DLP)
DLP solutions help organizations protect sensitive data from unauthorized access or exfiltration. DLP tools monitor and control data transfer across endpoints, ensuring that sensitive information remains secure.
3.6 Identity and Access Management (IAM)
IAM solutions provide centralized control over user identities and access privileges. Implementing IAM can help prevent unauthorized access to endpoints and sensitive data. Multi-factor authentication (MFA) is a critical component of IAM, adding an additional layer of security.
3.7 Encryption
Encryption is essential for protecting data stored on endpoints. Full-disk encryption (FDE) ensures that all data on a device is encrypted, making it inaccessible to unauthorized users. Data encryption in transit protects sensitive information as it moves across networks.
3.8 Security Information and Event Management (SIEM)
SIEM solutions aggregate and analyze security data from various sources, including endpoints. SIEM tools provide centralized visibility into security events, enabling organizations to detect and respond to threats more effectively.
Chapter 4: Best Practices for Endpoint Security
4.1 Implement a Layered Security Approach
A layered security approach, often referred to as “defense in depth,” combines multiple security measures to create a comprehensive defense against cyber threats. This approach helps to ensure that if one layer fails, others remain in place to protect endpoints.
4.2 Regular Software Updates and Patch Management
Keeping software up to date is crucial for preventing exploits targeting known vulnerabilities. Organizations should implement a robust patch management process to ensure that all endpoints receive timely updates.
4.3 Employee Training and Awareness
Educating employees about cybersecurity best practices is essential for preventing attacks. Training should cover topics such as recognizing phishing attempts, safe browsing habits, and the importance of strong passwords.
4.4 Strong Password Policies
Implementing strong password policies is vital for securing endpoints. Passwords should be complex, unique, and changed regularly. Organizations should encourage the use of password managers to help users manage their credentials securely.
4.5 Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide multiple forms of authentication before accessing endpoints or sensitive data. Implementing MFA significantly reduces the risk of unauthorized access.
4.6 Device Control and Management
Organizations should implement policies to control and manage the devices that connect to their networks. This includes ensuring that only authorized devices are allowed access and regularly auditing devices for compliance.
4.7 Continuous Monitoring and Threat Detection
Continuous monitoring of endpoints enables organizations to detect and respond to threats in real-time. Implementing EDR solutions and SIEM systems can provide visibility into endpoint activity and help identify suspicious behavior.
4.8 Incident Response Planning
Having a well-defined incident response plan is critical for addressing security incidents effectively. Organizations should regularly test and update their plans to ensure they can respond swiftly and efficiently to endpoint security breaches.
Chapter 5: Challenges in Endpoint Security
5.1 The Proliferation of Devices
The rapid increase in the number of devices connected to corporate networks, including personal devices in BYOD scenarios, complicates endpoint security management. Each device represents a potential attack surface that must be monitored and secured.
5.2 Sophistication of Cyber Attacks
Cybercriminals are continually developing more sophisticated attack methods, making it challenging for organizations to keep up. The emergence of advanced threats, such as APTs, requires more robust security measures.
5.3 Remote Work Challenges
The shift to remote work has expanded the attack surface and introduced new security challenges. Employees accessing corporate networks from home or public Wi-Fi networks may use unsecured devices, increasing the risk of breaches.
5.4 Resource Constraints
Many organizations face resource constraints that can hinder their ability to implement comprehensive endpoint security measures. Limited budgets and staffing can lead to gaps in security coverage.
5.5 Regulatory Compliance
Compliance with data protection regulations can be complex and resource-intensive. Organizations must navigate various requirements while ensuring that their endpoint security measures align with regulatory mandates.
Chapter 6: Future Trends in Endpoint Security
6.1 Artificial Intelligence and Machine Learning
The integration of AI and machine learning in endpoint security solutions will enhance threat detection and response capabilities. These technologies can analyze vast amounts of data, identify patterns, and predict potential threats, enabling organizations to respond proactively.
6.2 Extended Detection and Response (XDR)
XDR is an emerging security approach that integrates multiple security products into a cohesive solution. XDR provides centralized visibility and automated response capabilities across endpoints, networks, and cloud environments, streamlining threat detection and response.
6.3 Zero Trust Security Model
The zero trust model emphasizes never trusting any device or user by default, regardless of their location. This approach requires continuous verification of identities and devices, minimizing the risk of unauthorized access to endpoints.
6.4 Increased Focus on Mobile Endpoint Security
As mobile devices become an integral part of the workplace, organizations will need to prioritize mobile endpoint security. MDM solutions, app security, and user behavior analytics will play crucial roles in securing mobile endpoints.
6.5 Integration of Security Automation
Automation will become increasingly important in endpoint security, enabling organizations to respond to threats faster and more efficiently. Automated responses can help mitigate the impact of incidents and reduce the burden on security teams.
6.6 Privacy-Enhancing Technologies
As privacy regulations evolve, organizations will seek to implement privacy-enhancing technologies to protect sensitive data on endpoints. This includes techniques like data anonymization and tokenization to ensure compliance with data protection laws.
Conclusion
Endpoint security is an essential component of an organization’s overall cybersecurity strategy. As the digital landscape continues to evolve, the importance of protecting endpoints from cyber threats cannot be overstated. Organizations must adopt a proactive approach to endpoint security, implementing robust technologies, best practices, and continuous monitoring to safeguard their networks.
By understanding the various threats facing endpoints, leveraging advanced security solutions, and fostering a culture of security awareness, organizations can effectively mitigate risks and protect their digital assets. As technology advances, organizations must remain agile and adapt their endpoint security strategies to stay ahead of emerging threats, ensuring the safety and integrity of their data in an increasingly interconnected world.

