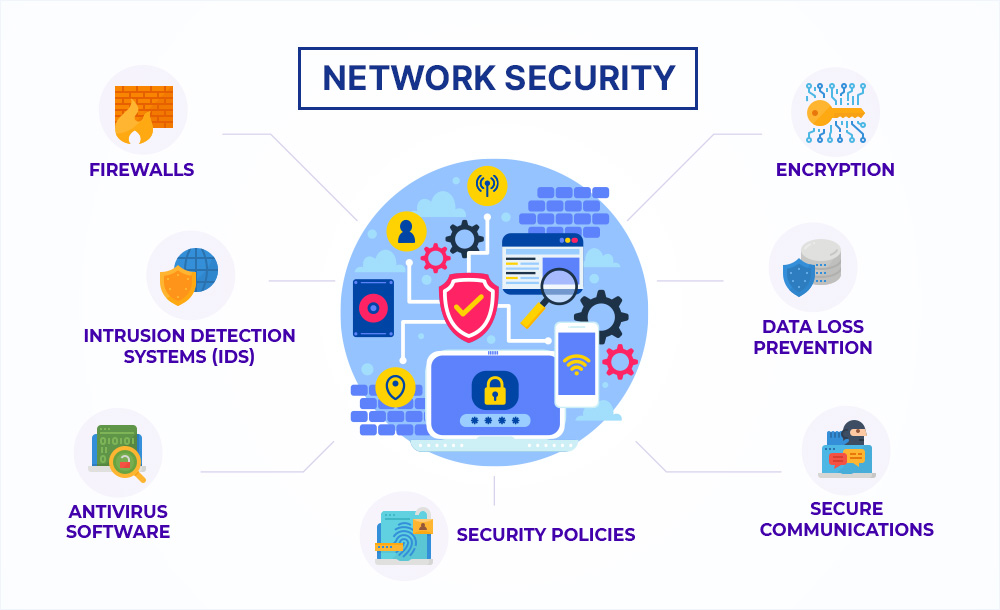
Network Security

What Is Network Security?

Network security is the protection of the underlying networking infrastructure from unauthorized access, misuse, or theft. It involves creating a secure infrastructure for devices, applications, users, and applications to work in a secure manner.
Contact Cisco
How does network security work?
Network security combines multiple layers of defenses at the edge and in the network. Each network security layer implements policies and controls. Authorized users gain access to network resources, but malicious actors are blocked from carrying out exploits and threats.
How do I benefit from network security?
Digitization has transformed our world. How we live, work, play, and learn have all changed. Every organization that wants to deliver the services that customers and employees demand must protect its network. Network security also helps you protect proprietary information from attack. Ultimately it protects your reputation.
Types of network security
Firewalls
A firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules. Cisco offers both threat-focused firewalls and unified threat management (UTM) devices.
Workload security
Workload security protects workloads moving across different cloud and hybrid environments. These distributed workloads have larger attack surfaces, which must be secured without affecting the agility of the business.
NetWORK security
NetWORK security is Cisco's vision for simplifying network, workload, and multicloud security by delivering unified security controls to dynamic environments.
Network segmentation
Software-defined segmentation puts network traffic into different classifications and makes enforcing security policies easier. Ideally, the classifications are based on endpoint identity, not mere IP addresses. You can assign access rights based on role, location, and more so that the right level of access is given to the right people and suspicious devices are contained and remediated.
VPN
A virtual private network encrypts the connection from an endpoint to a network, often over the internet. Typically, a remote-access VPN uses IPsec or Secure Sockets Layer to authenticate the communication between device and network.
Access control

Not every user should have access to your network. To keep out potential attackers, you need to recognize each user and each device. Then you can enforce your security policies. You can block noncompliant endpoint devices or give them only limited access. This process is network access control (NAC).
Anti-virus and anti-malware software
"Malware," short for "malicious software," includes viruses, worms, Trojans, ransomware, and spyware. Sometimes malware will infect a network but lie dormant for days or even weeks. The best antimalware programs not only scan for malware upon entry, but also continuously track files afterward to find anomalies, remove malware, and fix damage.
Application security
Any software you use to run your business needs to be protected, whether your IT staff builds it or whether you buy it. Unfortunately, any application may contain holes, or vulnerabilities, that attackers can use to infiltrate your network. Application security encompasses the hardware, software, and processes you use to close those holes.
- Full-stack Observability
- AppDynamics APM
- Cisco application-first products
- Security Advisory Services
Behavioral analytics
To detect abnormal network behavior, you must know what normal behavior looks like. Behavioral analytics tools automatically discern activities that deviate from the norm. Your security team can then better identify indicators of compromise that pose a potential problem and quickly remediate threats.
Cloud security
Cloud security is a broad set of technologies, policies, and applications applied to defend online IP, services, applications, and other imperative data. It helps you better manage your security by shielding users against threats anywhere they access the internet and securing your data and applications in the cloud.
Data loss prevention
Organizations must make sure that their staff does not send sensitive information outside the network. Data loss prevention, or DLP, technologies can stop people from uploading, forwarding, or even printing critical information in an unsafe manner.
Email security
Email gateways are the number one threat vector for a security breach. Attackers use personal information and social engineering tactics to build sophisticated phishing campaigns to deceive recipients and send them to sites serving up malware. An email security application blocks incoming attacks and controls outbound messages to prevent the loss of sensitive data.Network Security refers to the practices, technologies, and policies designed to protect the integrity, confidentiality, and availability of computer networks and data. It encompasses a wide range of strategies aimed at preventing unauthorized access, misuse, modification, or denial of a computer network and its resources. With the proliferation of cyber threats, network security is crucial for protecting not only enterprise networks but also personal data and government infrastructure.
In this detailed article, we will explore the key components, methodologies, common threats, and modern solutions in network security.
Key Principles of Network Security

Just like information security, network security is based on the CIA Triad: confidentiality, integrity, and availability. These principles guide the security policies, architecture, and processes used to secure network infrastructure.
1. Confidentiality
Confidentiality ensures that sensitive information is protected from unauthorized access. This applies to the data traveling across the network as well as the devices and systems that store it.
- Encryption: Data transmitted over the network is often encrypted to prevent interception and reading by unauthorized parties.
- Access Control: Ensures that only authorized users can access certain areas of the network or specific information.
- Authentication: Mechanisms such as passwords, tokens, and biometrics verify the identity of users before they access network resources.
2. Integrity
Integrity ensures that the data being transmitted over the network is accurate and has not been tampered with or altered in transit.
- Hashing: Data can be hashed before transmission to ensure that any unauthorized changes can be detected by comparing the original and received data hashes.
- Digital Signatures: Used to verify the authenticity and integrity of a message, software, or digital document.
3. Availability
Availability ensures that network resources are available to authorized users when needed. Network availability can be threatened by various factors, including cyberattacks, hardware failures, or natural disasters.
- Redundancy: Includes the use of backup systems or networks to ensure continued availability in case of failure.
- Load Balancing: Distributes network traffic across multiple servers to prevent overload and ensure efficient performance.
Types of Network Security Solutions
Network security involves a wide array of tools and strategies designed to protect the infrastructure from external and internal threats. Here are some of the most common types of network security solutions:
1. Firewalls
A firewall acts as a barrier between an internal trusted network and external untrusted networks, such as the internet. Firewalls monitor and control incoming and outgoing network traffic based on predefined security rules.
- Packet Filtering: Firewalls inspect packets entering or leaving the network and allow or block them based on IP addresses, protocols, and ports.
- Stateful Inspection: A more advanced type of firewall that tracks the state of active connections and makes decisions based on the context of the traffic.
- Next-Generation Firewalls (NGFW): Provide additional features, such as deep packet inspection, intrusion detection, and integration with threat intelligence feeds.
2. Intrusion Detection and Prevention Systems (IDPS)
IDPS are essential for detecting and preventing malicious activities on a network.
- Intrusion Detection Systems (IDS): These systems monitor network traffic for signs of potential malicious activity or policy violations, alerting administrators if suspicious activity is detected.
- Intrusion Prevention Systems (IPS): These systems actively block or reject malicious traffic in real-time before it can cause harm.
3. Virtual Private Networks (VPNs)
A VPN allows users to securely connect to a network over an unsecured network, such as the internet. VPNs encrypt the connection, making it difficult for unauthorized parties to eavesdrop on data being transmitted between a user’s device and the network.
- Remote Access VPNs: Enable individual users to securely connect to a network from remote locations.
- Site-to-Site VPNs: Connect entire networks, such as branch offices, to a central office over the internet using encrypted tunnels.
4. Network Access Control (NAC)
NAC solutions enforce security policies at the point where users and devices attempt to connect to the network. It ensures that only authorized and compliant devices can access network resources.
- Pre-Admission Control: Assesses the security posture of a device before allowing it onto the network (e.g., ensuring it has updated antivirus software).
- Post-Admission Control: Monitors the device’s activities once it has access to the network, and can block or restrict its access if it behaves suspiciously.
5. Anti-Malware and Antivirus Solutions
- Signature-Based Detection: Identifies known threats by comparing files against a database of virus signatures.
- Heuristic Analysis: Detects previously unknown malware by examining the behavior of files.
6. Data Loss Prevention (DLP)
DLP technologies help prevent sensitive data from being lost, leaked, or misused. DLP solutions monitor and control data transfers over the network to ensure sensitive information, such as credit card numbers or intellectual property, is not sent outside the organization without authorization.
- Network DLP: Monitors data as it moves across the network, scanning emails, instant messages, and file transfers for sensitive information.
- Endpoint DLP: Monitors and controls data stored on endpoint devices, such as laptops and smartphones.
7. Wireless Security
Wireless networks introduce additional security challenges because of the nature of radio communications. Wireless security focuses on protecting the data transmitted over wireless connections and preventing unauthorized access to the wireless network.
- Wi-Fi Protected Access (WPA/WPA2/WPA3): Encryption protocols that protect data transmitted over wireless networks.
- Rogue Access Point Detection: Identifies unauthorized access points that could allow malicious actors to intercept wireless traffic.
8. Email Security
Email is one of the most common vectors for network attacks, including phishing, spam, and malware. Email security solutions protect an organization’s email communications from threats.
- Spam Filters: Block unsolicited emails that could carry phishing or malware links.
- Email Encryption: Encrypts the content of email messages to ensure that they cannot be read by unauthorized recipients.
Common Network Security Threats
Network security faces a diverse range of threats that evolve continuously. Below are some of the most common threats faced by networks today:
1. Malware
Malware is any malicious software designed to harm or exploit a network or device. Examples include viruses, ransomware, worms, and spyware.
- Ransomware: Locks access to network files or systems until a ransom is paid.
- Worms: Self-replicating malware that spreads across networks, consuming bandwidth and potentially delivering a destructive payload.
2. Phishing and Social Engineering Attacks
Phishing attacks involve tricking users into providing sensitive information, such as login credentials or financial details, by impersonating a legitimate entity.
- Spear Phishing: A targeted form of phishing aimed at specific individuals or organizations.
- Business Email Compromise (BEC): Cybercriminals impersonate executives or trusted partners to trick employees into transferring money or confidential data.
3. Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks

A DoS attack floods a network or server with so much traffic that legitimate users cannot access the services. In a DDoS attack, the traffic comes from multiple compromised systems, making it harder to mitigate.
- Botnets: Networks of infected devices controlled by attackers to launch large-scale DDoS attacks.
- Mitigation: Solutions such as cloud-based DDoS protection, firewalls, and traffic filtering are used to absorb and deflect attack traffic.
4. Insider Threats
Insider threats occur when individuals within an organization misuse their access to the network for malicious purposes. These threats can come from employees, contractors, or partners with legitimate access to network resources.
- Privileged Access Misuse: Insiders with higher-level access can cause greater damage if they abuse their permissions.
- Accidental Insider Threats: Employees may inadvertently introduce malware or expose sensitive data by falling for phishing attacks or misconfiguring security settings.
5. Man-in-the-Middle (MitM) Attacks
- SSL Stripping: Downgrades HTTPS (encrypted traffic) to HTTP (unencrypted traffic), allowing attackers to view sensitive information.
- Prevention: Strong encryption protocols, VPNs, and secure browser practices help prevent MitM attacks.
6. Zero-Day Exploits

A zero-day exploit targets previously unknown vulnerabilities in software or hardware, allowing attackers to infiltrate the network before the vendor has released a patch.
- Vulnerability Scanning: Regularly scanning for vulnerabilities can help identify weaknesses before they can be exploited.
- Patch Management: Keeping software and hardware up to date with the latest security patches can mitigate the risk of zero-day exploits.
Best Practices for Network Security
To effectively secure a network, organizations must implement a layered approach that incorporates various technologies and policies. Below are some best practices for network security:
1. Implement a Strong Firewall
A firewall should be the first line of defense for a network. It helps prevent unauthorized access by monitoring and controlling incoming and outgoing traffic.
Update Firewall Rules: Regularly review and update firewall rules to reflect changes in network infrastructure and emerging threats.


People find it much more appealing to view dressed carcasses than covered ones.
And a portion of the appeal is the frailty that comes with being shirtless and
feeling a little uncomfortable or exposed
during pleasure. When both celebrations are buff, it increases the connection of sexual.
When their partner is defenseless, dominance
is specifically appealing to some folks. And let’s not forget about the nude video: they really go all out
when it comes to showing off anything, focusing on infiltration, and on private
components. http://demo.html5xcss3.com/demo.php?url=sk.tags.world%2Fkosice%2Findex.php%3Fpage%3Duser%26action%3Dpub_profile%26id%3D641190
People find it much more appealing to view dressed carcasses than covered ones.
And a portion of the appeal is the frailty that comes with being shirtless
and feeling a little uncomfortable or exposed during pleasure.
When both celebrations are buff, it increases the connection of
sexual. When their partner is defenseless, dominance is
specifically appealing to some folks. And let’s not forget about the
nude video: they really go all out when it comes to showing
off anything, focusing on infiltration, and on private components. http://demo.html5xcss3.com/demo.php?url=sk.tags.world%2Fkosice%2Findex.php%3Fpage%3Duser%26action%3Dpub_profile%26id%3D641190
Přijetí hypoteční platby může být
nebezpečné pokud nemáte rádi čekání v dlouhých řadách , vyplnění závažné formuláře
, a odmítnutí úvěru na základě vašeho úvěrového skóre .
Přijímání hypoteční platby může být problematické, pokud nemáte rádi čekání v dlouhých řadách ,
podávání extrémních formulářů , a odmítnutí
úvěru na základě vašeho úvěrového skóre .
Přijímání hypoteční platby může být problematické ,
pokud nemáte rádi čekání v dlouhých řadách , vyplnění extrémních formulářů a odmítnutí úvěrových rozhodnutí založených na úvěrových skóre .
Nyní můžete svou hypotéku zaplatit rychle a efektivně v České republice. https://groups.google.com/g/sheasjkdcdjksaksda/c/XO0pnSI6fHg
Přijetí hypoteční platby může být
nebezpečné pokud nemáte rádi čekání v dlouhých řadách , vyplnění závažné formuláře
, a odmítnutí úvěru na základě vašeho úvěrového
skóre . Přijímání hypoteční platby může být
problematické, pokud nemáte rádi čekání v dlouhých řadách
, podávání extrémních formulářů , a
odmítnutí úvěru na základě vašeho úvěrového skóre .
Přijímání hypoteční platby může být problematické , pokud nemáte rádi čekání v dlouhých řadách , vyplnění
extrémních formulářů a odmítnutí úvěrových rozhodnutí založených na úvěrových
skóre . Nyní můžete svou hypotéku zaplatit rychle a efektivně v České republice. https://groups.google.com/g/sheasjkdcdjksaksda/c/XO0pnSI6fHg