
Introduction to Threat Intelligence
Threat intelligence involves the collection, analysis, and interpretation of data regarding potential or ongoing cyber threats. It allows security teams to make informed decisions about how to protect their organization against cyberattacks. This article aims to provide an in-depth exploration of threat intelligence, its types, sources, lifecycle, benefits, challenges, and best practices for organizations.
Understanding Threat Intelligence
Cyber threat intelligence allows organizations to move beyond reactive security measures to adopt a proactive approach, enabling them to anticipate and mitigate attacks before they occur. For example, if an organization learns about a new vulnerability that attackers are exploiting, they can apply patches or implement other protective measures before the attack reaches them.
Types of Threat Intelligence
There are several categories of threat intelligence, each serving different purposes for various stakeholders within an organization. These types include:
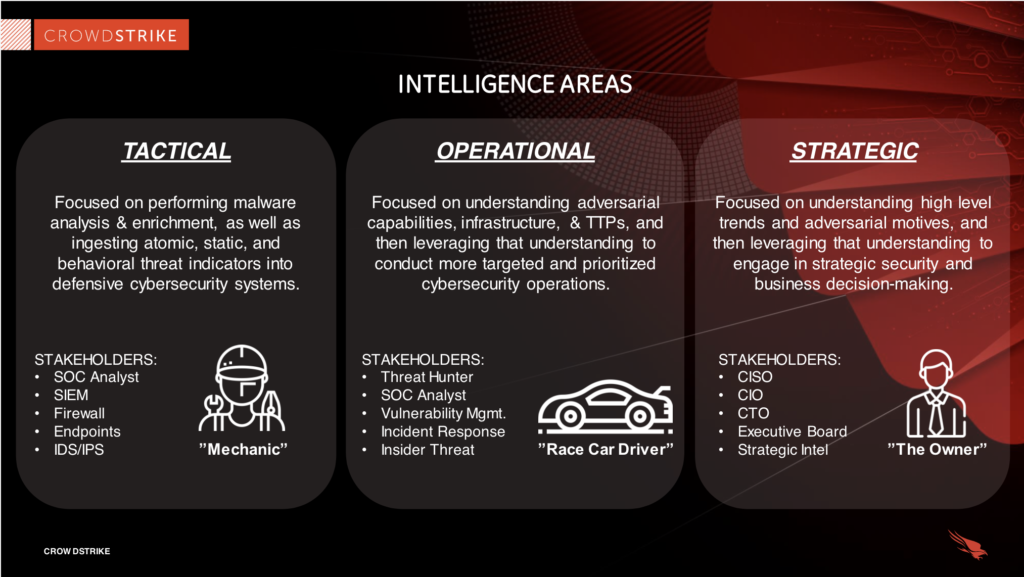
- Strategic Threat Intelligence: This type of intelligence provides high-level insights into the broader cybersecurity landscape, such as emerging threats, geopolitical factors, and industry-specific risks. Strategic threat intelligence is aimed at decision-makers and executives who need to make informed business decisions about risk management and resource allocation. It is often presented in the form of reports, trend analyses, or threat assessments.
- Tactical Threat Intelligence: Tactical intelligence focuses on the specific tactics, techniques, and procedures (TTPs) that adversaries use to carry out cyberattacks. It is often technical in nature and provides security teams with actionable information to detect, prevent, or mitigate attacks. This includes details about malware, phishing campaigns, ransomware variants, and exploits used by attackers.
- Operational Threat Intelligence: Operational intelligence focuses on information about ongoing attacks, typically collected in real time. This type of intelligence helps security operations teams (SOCs) detect and respond to attacks quickly and efficiently. Operational threat intelligence is crucial for incident response and threat hunting.
- Technical Threat Intelligence: This type of intelligence provides highly specific information about technical indicators of an attack, such as IP addresses, file hashes, domain names, and malware signatures. Technical threat intelligence is useful for security analysts and engineers who need to configure detection tools, firewalls, and intrusion prevention systems (IPS) to block malicious activity.
Sources of Threat Intelligence
Threat intelligence data is gathered from various sources, both internal and external. These sources can include:
- Internal Security Logs: Organizations can leverage their own security logs from firewalls, intrusion detection systems (IDS), and security information and event management (SIEM) platforms. Analyzing patterns in these logs can help identify potential threats within their environment.
- Open Source Intelligence (OSINT): OSINT involves collecting data from publicly available sources such as websites, blogs, social media, and cybersecurity forums. OSINT provides valuable information about emerging threats, vulnerabilities, and trends in the cyber threat landscape.
- Dark Web Monitoring: Cybercriminals often trade or sell stolen data, exploits, and malware on dark web marketplaces. Monitoring these sources provides insights into potential attacks targeting specific industries or organizations.
- Threat Feeds: Threat feeds are data streams that provide continuous updates on known threats, such as IP addresses of malicious actors, phishing domains, and malware signatures. These feeds come from commercial vendors or community-driven platforms like VirusTotal or AlienVault.
- Security Vendors: Many cybersecurity companies offer commercial threat intelligence services. These vendors often have access to large databases of threat data, collected from their customer base, honeypots, or proprietary research.
- Government and Law Enforcement Agencies: Governments and international organizations, such as CERT (Computer Emergency Response Team) and law enforcement agencies, also provide valuable threat intelligence through alerts and advisories on cyber threats targeting critical infrastructure and industries.
The Threat Intelligence Lifecycle
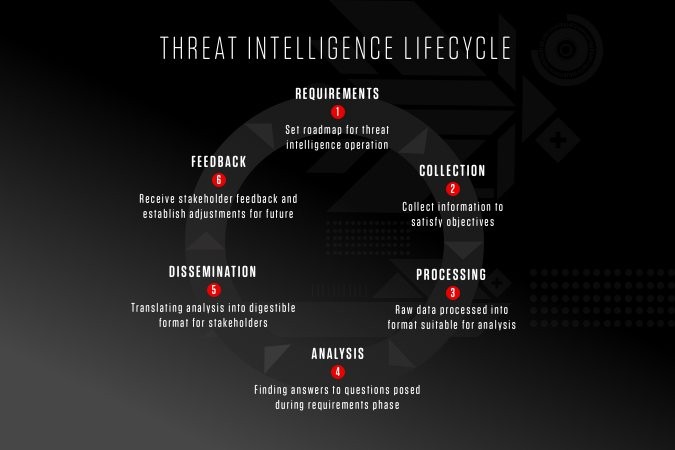
The process of gathering and using threat intelligence follows a structured lifecycle, ensuring that the intelligence is relevant, actionable, and timely. This lifecycle consists of six stages:
- Requirements: The first stage involves identifying what the organization needs to know. The security team, in collaboration with leadership, defines the intelligence requirements based on the organization’s risk profile, industry, and business objectives.
- Collection: Once the intelligence requirements are defined, data is collected from various internal and external sources. This data could include logs, network traffic, malware samples, or threat reports.
- Processing: The collected raw data is often vast and unstructured. During this stage, it is cleaned, normalized, and organized into a usable format for further analysis. This may involve filtering out false positives or irrelevant information.
- Analysis: In this stage, the processed data is analyzed to generate actionable intelligence. Analysts look for patterns, correlations, and emerging threats, interpreting the data to provide insights into potential risks.
- Dissemination: The final intelligence product is then shared with the appropriate stakeholders within the organization. This could include SOC teams, incident response teams, or executive leadership. The intelligence should be presented in a format that is understandable and actionable for the audience.
- Feedback: After the intelligence is delivered, feedback is gathered to assess its effectiveness. Was it timely? Did it provide actionable insights? Based on this feedback, the intelligence process can be refined and improved for future use.
Benefits of Threat Intelligence
Effective threat intelligence provides organizations with several key benefits:
- Proactive Defense: Threat intelligence enables organizations to stay ahead of cybercriminals by identifying potential threats before they escalate into full-blown attacks. By understanding the threat landscape, security teams can prioritize vulnerabilities, apply patches, and enhance security controls preemptively.
- Enhanced Incident Response: During an attack, threat intelligence provides real-time insights into the methods and tools being used by adversaries. This allows incident response teams to take swift and targeted actions, reducing the impact and duration of the attack.
- Improved Decision-Making: Strategic threat intelligence provides executives and decision-makers with a clearer understanding of the risks their organization faces. This allows them to make informed decisions about resource allocation, risk management, and security investments.
- Reduced False Positives: Threat intelligence can help refine detection systems, reducing the number of false positives that security teams need to investigate. By providing accurate, contextual information about known threats, security teams can focus on genuine risks rather than chasing benign alerts.
- Industry-Specific Insights: Many threat actors target specific industries, such as finance, healthcare, or manufacturing. Threat intelligence can provide industry-specific insights, helping organizations understand the threats most relevant to them and prepare accordingly.
Challenges in Implementing Threat Intelligence

While the benefits of threat intelligence are significant, organizations face several challenges when trying to implement it effectively:
- Data Overload: The sheer volume of threat data available can be overwhelming. Without proper tools and processes, security teams may struggle to sift through the noise and identify relevant threats.
- Lack of Skilled Analysts: Threat intelligence requires skilled analysts who can interpret complex data and provide actionable insights. However, there is a global shortage of cybersecurity professionals, making it difficult for organizations to build experienced threat intelligence teams.
- Integration with Existing Systems: Integrating threat intelligence with existing security tools, such as SIEM platforms or firewalls, can be challenging. Without proper integration, threat intelligence may not be fully utilized or actionable.
- Cost: Commercial threat intelligence services can be expensive, especially for smaller organizations. While free or community-driven threat feeds exist, they may lack the depth or reliability of paid services.
- Timeliness: In the fast-moving world of cybersecurity, threat intelligence must be timely to be useful. Outdated or stale intelligence can lead to missed opportunities for mitigation or worse, a false sense of security.
Best Practices for Threat Intelligence

To maximize the effectiveness of threat intelligence, organizations should adhere to the following best practices:
- Define Clear Objectives: Before implementing a threat intelligence program, organizations should clearly define their goals. Are they trying to improve incident response? Reduce vulnerability to phishing attacks? Understanding the specific objectives helps guide the focus of intelligence gathering.
- Automate Where Possible: Given the large volume of data, automating parts of the threat intelligence process is crucial
- n the rapidly evolving world of cybersecurity, staying ahead of cyber threats has become increasingly complex and vital. Threat intelligence has emerged as a key component of modern cybersecurity strategies, providing the necessary information to help organizations proactively protect their digital assets. It involves the collection and analysis of data to identify existing or potential threats and delivering actionable insights to mitigate or prevent attacks.
This article explores threat intelligence in-depth, covering its definition, key components, types, applications, and best practices for implementation.
Understanding Threat Intelligence
1. Definition of Threat Intelligence Threat intelligence (TI) refers to the process of collecting, analyzing, and interpreting data regarding potential or current threats to an organization’s cybersecurity. The goal is to transform raw data into actionable intelligence that helps security teams understand and respond to cyber threats, allowing organizations to make informed decisions about threat mitigation and response strategies.
Rather than simply reacting to an incident, threat intelligence enables organizations to anticipate, prepare for, and defend against cyber threats more effectively.
2. The Importance of Threat Intelligence The value of threat intelligence lies in its ability to provide context about the various cyber threats targeting an organization. Instead of being overwhelmed by vast amounts of data, organizations can leverage TI to:
Understand the motives and techniques of attackers.
Identify vulnerabilities in their systems.- Stay up to date on emerging threats and attack vectors.
Mitigate risks before they escalate into breaches.
In essence, threat intelligence bridges the gap between raw data and practical security actions, making it a critical tool in the fight against cybercrime.
Types of Threat Intelligence
Threat intelligence is categorized based on the type of data collected and the depth of analysis. These categories help organizations tailor their approach depending on their specific security needs.
1. Strategic Threat Intelligence
Definition: High-level intelligence focused on broad trends, risks, and patterns in cybersecurity.
Audience: Senior executives, decision-makers, and board members.
Content: Strategic intelligence provides a macro-level view of the threat landscape. It includes reports on emerging trends, geopolitical analysis, and long-term risks to an organization’s industry or region.
Application: Used for long-term decision-making and shaping overall cybersecurity policies. It helps leadership understand potential future threats and allocate resources effectively.
2. Tactical Threat Intelligence
Definition: Intelligence that focuses on specific threats or adversarial techniques, tactics, and procedures (TTPs).
Audience: Security analysts and incident response teams.
Content: Tactical intelligence provides detailed information on how attacks are carried out, including indicators of compromise (IoCs), malware analysis, and phishing techniques.
Application: Primarily used for immediate defense actions, such as patching vulnerabilities or modifying firewall rules to block known malicious activities.
3. Operational Threat Intelligence
Definition: Real-time intelligence focused on active cyber threats targeting an organization.
Audience: Security operations centers (SOCs) and incident response teams.
Content: Operational intelligence includes information about ongoing attacks, specific threat actors, and their current campaigns.
Application: Enables organizations to respond quickly to active threats and reduce the time attackers spend in their environment.
4. Technical Threat Intelligence
Definition: Low-level technical data used to detect and block cyber threats.
Audience: Security engineers and system administrators.
Content: Technical intelligence includes details like malware signatures, IP addresses, domain names, and hash values associated with specific threats.
Application: It supports threat detection and mitigation by integrating this data into security tools like intrusion detection systems (IDS) or endpoint protection software.
Sources of Threat Intelligence
Threat intelligence comes from a variety of sources, both internal and external. Here’s a look at some common sources:
1. Internal Sources
Network logs: Logs from firewalls, routers, and servers provide valuable data on anomalies or suspicious activities.
Endpoint detection systems: These tools monitor devices within an organization’s network for threats.
Incident reports: Previous cybersecurity incidents can offer insights into vulnerabilities and attack methods.
2. External Sources
Open-source intelligence (OSINT): Publicly available data, such as threat reports, forums, blogs, and news sites, can provide valuable information on emerging threats.
Commercial threat intelligence services: Many vendors offer subscription-based services that provide access to curated threat intelligence feeds.
Dark web monitoring: The dark web is a haven for cybercriminals, and monitoring it for discussions about vulnerabilities, exploits, or leaked credentials can be crucial.
Sharing platforms and communities: Threat intelligence is often shared between organizations through industry-specific groups like Information Sharing and Analysis Centers (ISACs) and platforms like the Cyber Threat Alliance (CTA).
Applications of Threat Intelligence
Threat intelligence is used across various aspects of an organization’s cybersecurity strategy. Some common applications include:
1. Threat Hunting
Threat hunters use intelligence to proactively search for hidden threats in a network. By analyzing patterns and IoCs, hunters can identify potential risks before they evolve into full-blown incidents.
2. Incident Response
In the event of a security breach, threat intelligence is essential for identifying the attackers, understanding their methods, and mitigating damage. Operational and technical intelligence provide immediate insights into how to contain and eradicate the threat.
3. Vulnerability Management
Vulnerability management involves identifying and patching vulnerabilities in an organization’s systems. Threat intelligence helps prioritize these efforts by highlighting which vulnerabilities are most likely to be exploited by attackers.
4. Security Awareness Training
Threat intelligence can inform employee training programs by providing real-world examples of phishing attacks, social engineering tactics, and other threats that employees need to recognize and avoid.
5. Risk Management
By offering insights into the latest cyber threats, threat intelligence can help organizations better assess and manage their cybersecurity risks. Decision-makers can allocate resources more efficiently and prioritize critical assets based on potential threats.
Challenges in Implementing Threat Intelligence
While threat intelligence offers immense benefits, it also presents certain challenges that organizations need to address:
1. Data Overload
One of the most significant challenges is dealing with the sheer volume of data. Without proper filtering and analysis, organizations may be overwhelmed by the influx of information, leading to decision fatigue or missed threats.
2. False Positives
Excessive false positives can waste time and resources. Ensuring that threat intelligence is accurate and relevant is crucial to avoid focusing on non-threats while real threats go unnoticed.
3. Integration with Existing Systems
Many organizations face difficulties integrating threat intelligence feeds into their existing cybersecurity tools and processes. A fragmented security architecture can hinder the full potential of threat intelligence.
4. Lack of Skilled Personnel
Threat intelligence requires skilled cybersecurity professionals who can analyze data and translate it into actionable steps. The shortage of skilled personnel in cybersecurity presents a major challenge for many organizations.
5. Cost of Threat Intelligence Solutions
Subscription-based threat intelligence services can be expensive, especially for small and medium-sized organizations. Balancing the cost of intelligence solutions with their effectiveness is a common struggle.
Best Practices for Effective Threat Intelligence Implementation
To maximize the value of threat intelligence, organizations should follow these best practices:
1. Set Clear Objectives
Define the specific goals of your threat intelligence program. Are you focused on early detection, incident response, or vulnerability management? Clear objectives will guide your intelligence gathering and analysis efforts.
2. Leverage Multiple Sources
Rely on a mix of internal and external intelligence sources. Combining OSINT, commercial threat feeds, and community-shared intelligence provides a more comprehensive view of the threat landscape.
3. Automate Where Possible
Use automation tools to collect, analyze, and filter large volumes of threat data. This reduces the risk of data overload and allows security teams to focus on more complex, high-priority threats.
4. Contextualize the Intelligence
Raw data without context isn’t useful. Ensure that threat intelligence is relevant to your organization’s industry, geography, and specific infrastructure to make it actionable.
5. Integrate with Your Security Infrastructure
Integrate threat intelligence into existing security tools like firewalls, intrusion detection systems, and security information and event management (SIEM) platforms. This allows for real-time threat detection and response.
6. Collaborate and Share
Threat intelligence thrives on collaboration. Join industry-specific sharing groups, such as ISACs, to stay updated on emerging threats and share intelligence with peers.
7. Train Your Team
Ensure that your security team is well-trained in using threat intelligence tools and techniques. Regular training sessions and workshops can help your team stay sharp and proactive in identifying threats.
8. Regularly Update Your Threat Intelligence Strategy
Cyber threats evolve rapidly, and so should your threat intelligence strategy. Regularly review and update your approach based on new threats, tools, and technologies.

